Authentication Gateway
- Optimize Bandwidth
- Improve Network speed
- Increase Productivity
- Save Time
- Reduce Cost
Internet Authentication Gateway from CLEON provides a convenient method of controlling access to public and private networks leveraging existing network technologies. Users simply “open and connect” using their favorite browser and a login page pops-up prompting for authentication credentials before logon to the network.
The Authentication Gateway essentially acts as the gatekeeper by determining who has access to the network apart from a myriad of features including but not limited to Bandwidth Management, Access Control, Proxy, etc. As a bandwidth manager the gateway apportions pre-determined bandwidth per user or per device. This ensures that one single user or device does not consume the entire bandwidth available to the corporate office.

The primary benefits of this solution stems from the seamless connectivity not requiring additional customer knowledge, software or special configuration. Clients are able to quickly and easily gain access to the network regardless of the type of device, operating system or connectivity media used as long as the right credentials are supplied.
The authentication gateway can also serve managerial functions of redirecting users to a particular page to acquaint the users with special information, notices or a sign-up process. This can also be a good avenue to remind users of certain organizational policy.
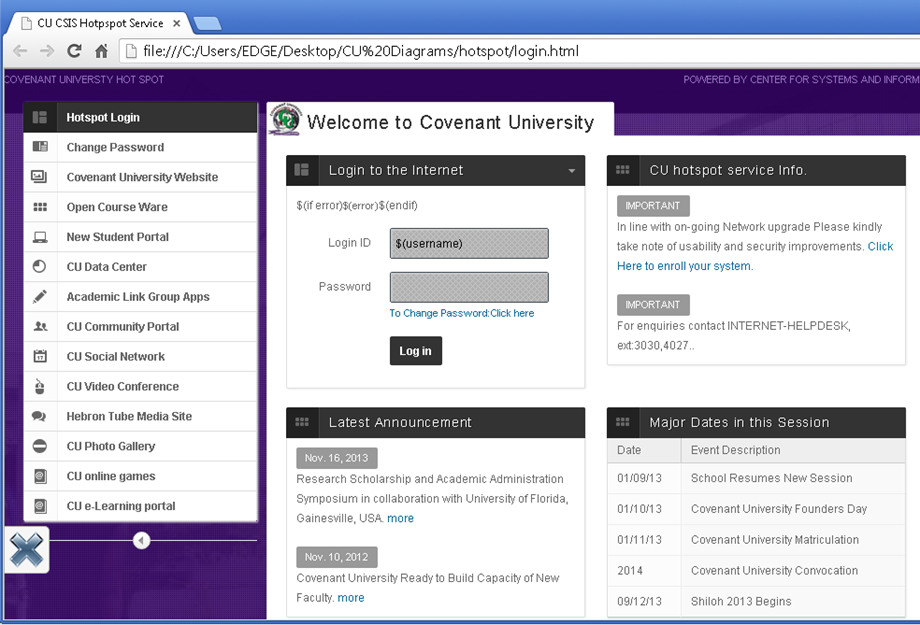
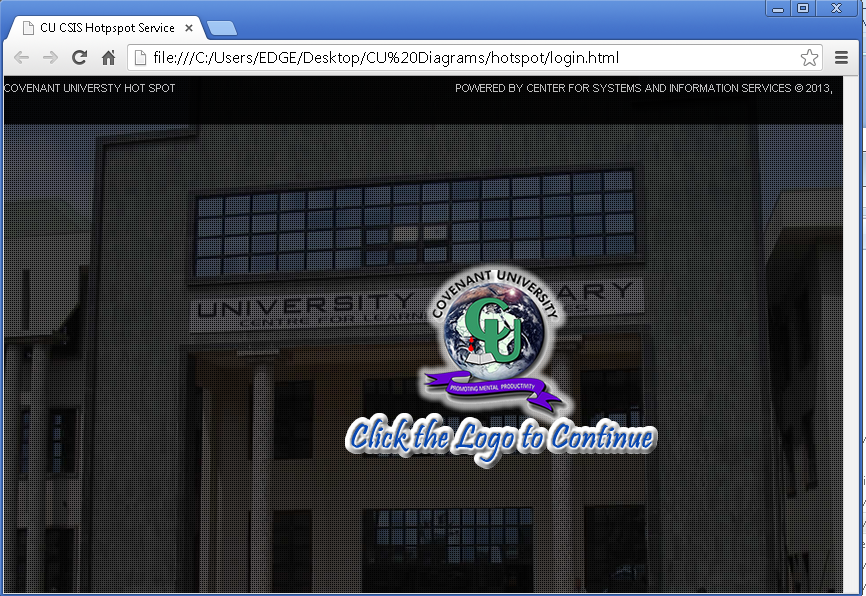
The Internet Authentication Gateway is uniquely suitable for a wide range of environments including offices, hotels, service providers, universities, Internet Hotspots and guest networks. The IAG is industry compliant and supports various authentication billing and management databases particularly those based on the RADIUS protocol.
The following is a table of notable features of the authentication gateway when combined with the User Manager. The user manager is a licensed database of policies that can be applied to user profiles that allows granular control of user accounts in the database.
FEATURES | BENEFITS |
Single server supports thousands of concurrent sessions | Optimize large scale deployments |
Browser based password encryption | Provides increased logon password security in addition to SSL encryption |
SSL Encryption | Industry standard for encryption and mutual authentication. Establishes identity, protects sensitive client information such as account passwords. |
Configurable Web HTML interface | Customize the look and feel, link to sign-up server, account management and advertising sites |
User status display | Allows users to view account statistics such as time and data used and remaining. |
Integrated ADMIN interface | Easy to use 100% web based configuration and local account management simplifies system configuration tasks. |
Active session list | See who’s online including duration and real-time bandwidth usage. Enables disconnect of active sessions. |
Setup a walled garden | Provides complimentary limited access to select services such as new customer signup, account management, company web sites or information related to a particular venue. |
Themes | Offer customized login portals based on user location, language, browser and device type. Operate multiple specialized venues concurrently on single server instance. |
Local account management | Configure local access accounts with expiration date, time & data limits and maximum upload/download data rates. Useful for smaller installations or special administrative access. |
Anonymous Access | Provides guest access to the network with an optional set of limitations such as upload/download data rates and daily time and data usage restrictions. This is useful in situations where you may want to provide a certain level of free service such as one or two hours of service per day, offer advertising supported access or simply require users read and accept a terms of service agreement before gaining access to the network. |
Client Data Mirroring | Captures all network data sent or received on per user basis to industry standard capture files. Useful for diagnostic or intercept purposes. |
Transparent web proxy | Directs HTTP requests to local transparent proxy servers on a per user basis. Enables customer choice of acceleration and content filtering services. |
Maximum prioritized UL/DL data rates per user | Prevents single users from monopolizing network resources. Enables tiered service offerings. |
Bandwidth pooling | Restrict groups of users to common shared bandwidth allocations. Prevents single users from monopolizing network resources. Enables tiered service offerings. |
Commercial session interruption | Periodically force users to view a series of commercial messages. Advertising supported access. Tiered service offerings. |
Tickets/Vouchers | Revenue generation/Managed access |
Traffic Quotas | Limits users/devices to amount of download/upload per day/week/month |
SUMMARY
Internet Bandwidth is a premium resource and must be treated as such by putting control measures that prevents abuse, guarantees fair-share usage and prevents unauthorized access. Putting control measures also ensures that workers are focused on the more important tasks thus improving productivity.
ORDER INFORMATION
ITEM No | DESCRIPTION | |
IAG-NM-25 | Internet Authentication Gateway | |
RUM-NM-UL | User Manager |